An Overview Into Ransomware
Introduction
If you ever keep a close eye on the news headlines, you will probably notice that ransomware attacks are one of the top threat variants this country and the world have ever faced. The worst of it came in 2021, at the height of the COVID-19 pandemic, with attacks peaking in Q4 2021. During 2022, while attacks have continued, we have observed a slight downturn in Q1 2022 . However, some of them have been particularly insidious, focusing on hospitals and schools. A recent example is the attack on the Los Angeles Unified School District, the second largest in the country, which has already led to significant data leaks. According to the company Emsisoft, who tracks ransomware incidents, there have been 27 districts and over 1,735 schools hit by ransomware just in 2022. A key reason why this keeps happening is because both hospitals and schools need to keep running, and so many end up paying up and being profitable for hackers. The majority of districts do not have personnel dedicated to preventing and stopping cybersecurity threats, or unified standards. Until schools materially bolster their security, this is unlikely to stop.
But what exactly is a ransomware attack? If you have been a victim of one, you will know quite well the frustrating and costly outcomes. But if not, we will give you some of the highlights of it in this article.
What Ransomware Is All About
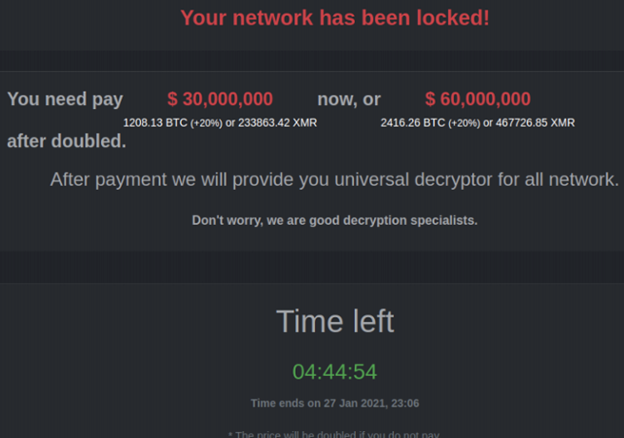
A ransomware attack is exactly what it sounds like. A cyberattacker from a nation-state threat actor (such as Russia, China, North Korea, etc.) launches a malicious payload that takes over your computer. It locks it up and all of the files that reside within it. In turn, your screen will usually display something like "We have hijacked your computer. You have 24 hours to make payment, and in return, we will give you the key to unlock both your computer and files".
The first thing that comes to mind is to make payment as quickly as possible. But before you do that (and it is recommended that you do not), there are some important things to consider:
- The cyberattacker or hacking group wants to be paid via virtual currency. The primary reason for this is that if a traditional currency is to be used, it can easily be tracked. The bad actor will most likely request that you make the payment via Bitcoin (as this is the preferred payment method). If you are not familiar with the virtual currency world, it can take quite some time for you to get this money rounded up.
- Once you have made payment, there is no guarantee whatsoever that you will receive the unlocking mechanism for your computer and the files. The cyberattacker will likely simply disappear somewhere and prey on another unsuspecting victim. But there have actually been a few hacking groups that have lived up to their pledge and have delivered the tools you need for unlocking. But this is a dicey situation to be in. If you pay and get your items in return, there is an excellent chance the cyberattacker will come back after you again because they now know where your vulnerabilities and weak spots are. Who knows, in this second round, they may even ask for more than your business can afford.
- Paying off the cyberattacker like this is becoming a crime in itself. For example, the US Federal Government can charge you with treason if you make payment to any of the nations that are deemed state threat actors. Also, many insurance companies will not even pay out your claim if you do make a ransom payment. But exceptions have been made, especially if the attack involved Critical Infrastructure. An excellent example of this is the Colonial Gas Pipeline hack. In the end, the CEO agreed to pay the $4 million ransom just to keep the flow of natural gas moving. Had this not happened, it is quite likely that flow of natural gas would have been abruptly halted, causing prices to spike even higher.
How To Minimize the Risk
You may be asking next, what can you do to prevent being a victim of a ransomware attack? The truth of the matter is there is nothing you can do directly. We are all at risk from the above situation happening. The key is how to lessen the odds or mitigate that risk from happening to you and your business. Here are some essential tips to keep in mind:
- Being meticulous about patching your systems:
By enabling MFA broadly throughout your organization, including for applications and accounts that access important services, you will disrupt attacks and make it more difficult for malicious actors to move across the network even if they managed to get their hands of some passwords. - MFA (multi-factor authentication):
By enabling MFA broadly throughout your organization, including for applications and accounts that access important services, you will disrupt attacks and make it more difficult for malicious actors to move across the network even if they managed to get their hands of some passwords.
- Always keep backups on a daily schedule:
Thus, if you are hit, all you technically have to do is to replace the hardware that has been affected and restore those with the backups. In this manner, it is highly recommended that you keep one set on-site and the other offsite, just so that you have some level of redundancy at hand.
- Think about moving to an on-cloud infrastructure:
With this, you will have all the tools you need to create backups automatically. The two providers that offer all you need in this regard are Microsoft Azure and AWS. What is advantageous here is that you will not be dealing with hardware directly. Instead, you will be creating what is known as Virtual Machines (aka VMs), which are the software emulations of the hardware. So, if any of these VMs are impacted by a security breach, you can quickly delete them and create brand new VMs in just a few minutes.
Conclusions
Although the total number of ransomware attacks has dissipated this year (which is good news), the bad news is that the magnitude of severity will only get worse. For example, cyberattackers are now launching extortion attacks after they take control of your computer. Meaning they can take any confidential information and data on it and expose it to the public unless you pay up. Or worse yet, they can take it and sell it on the Dark Web for a rather nice profit. Make sure you’re taking the above precautions to mitigate your cyberattack risk and continue to educate yourself and your colleagues on best practices.
If you are less than 100% confident in your cybersecurity program, I would love to have a conversation with you. Please contact us at sales@sprucetech.com to learn more.

